System misconfiguration is the number one vulnerability, at least for Mastodon

One time during a security engineering interview someone asked me
What is the number one vulnerability?
That question caught me by surprise. I immediately start thinking about OWASP top 10, RCE, 0days and things like that, then I remembered the security incidents I’ve deal with in the past and most of them has been related to employees accidentally exposing credentials or private keys so I responded with “developers pushing credentials into public repositories".
The interviewer smiled at me, she liked my answer, but clearly I was wrong. She said
The number one vulnerability is system misconfiguration
Today I’m going to explain why this is true and how I could have replaced everyone’s profile picture (or any other user’s uploaded content) with a meme at infosec.exchange Mastodon instance.
With all the drama happening lately on Twitter I decided to look at Mastodon. Mastodon is a free and open-source distributed social network which is super cool by itself. Most of the CyberSecurity people from twitter are gathering at infosec.exchange now so I went there and created an account.
Within minutes I start receiving greetings :). Then I start wondering (my hacker mind started kicking in) where is all this user uploaded content stored?
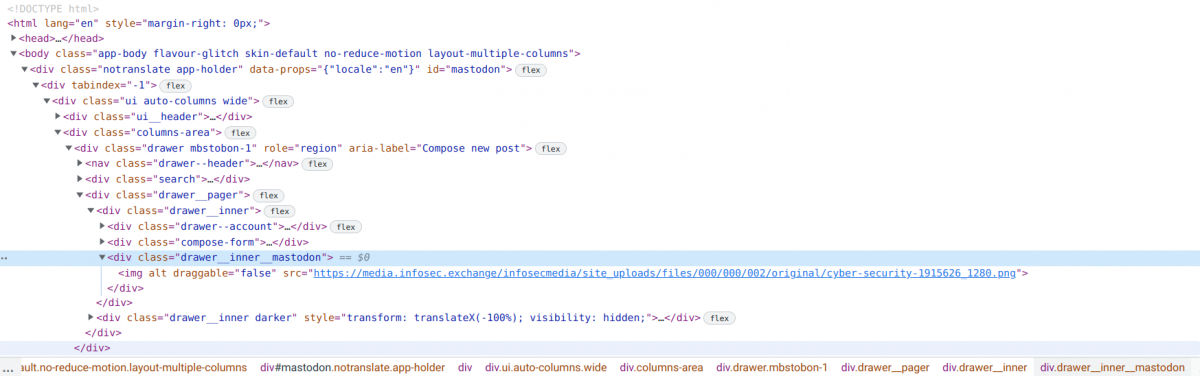
A quick look at the source code of the page reveals the content is coming from https://media.infosec.exchange/infosecmedia and when I visited the URL on my browser I found this
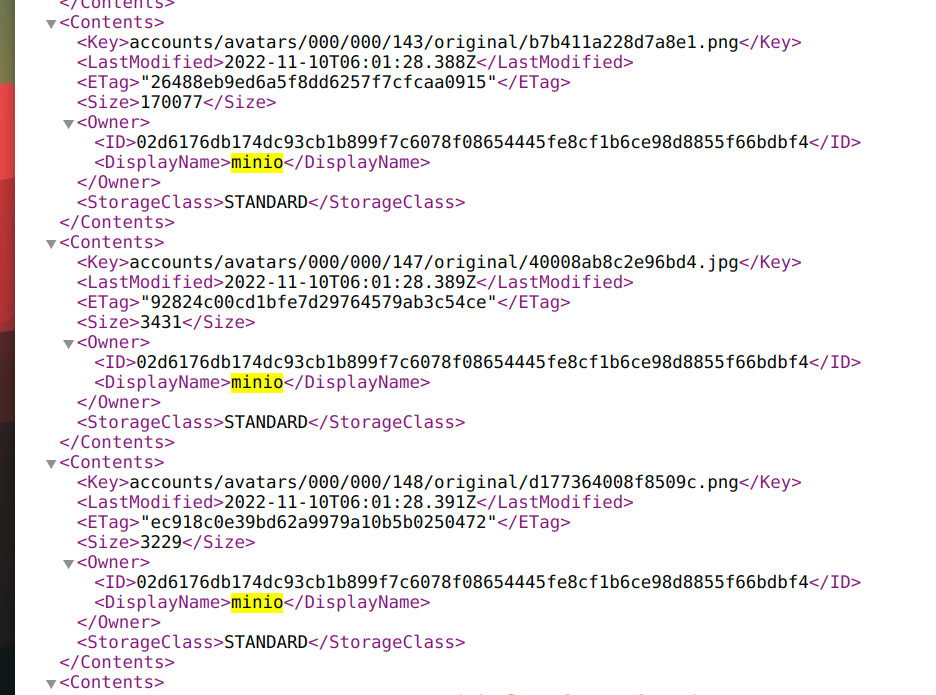
This looks very familiar to an AWS S3 xml response, also “minio" is displayed on the response as well so I immediately knew infosec.exchange was using MinIO.
Full disclosure, at the time of this publication on 11/18/2022, I’m working as a Security Software Engineer at MinIO. I’m very proud our product is being used by millions around the globe and with Mastodon getting a lot of adoption MinIO will only increase in popularity.
Anyways, my hacker mind (again) started wondering.
- User content is uploaded to MinIO buckets
- Buckets must have anonymous read access in order for the browser, or really any other client, to access those resources
- Can I query those resources using a tool like the MinIO Client?
I opened my terminal and typed
mc alias set infosec https://media.infosec.exchange/ "" "" --debug
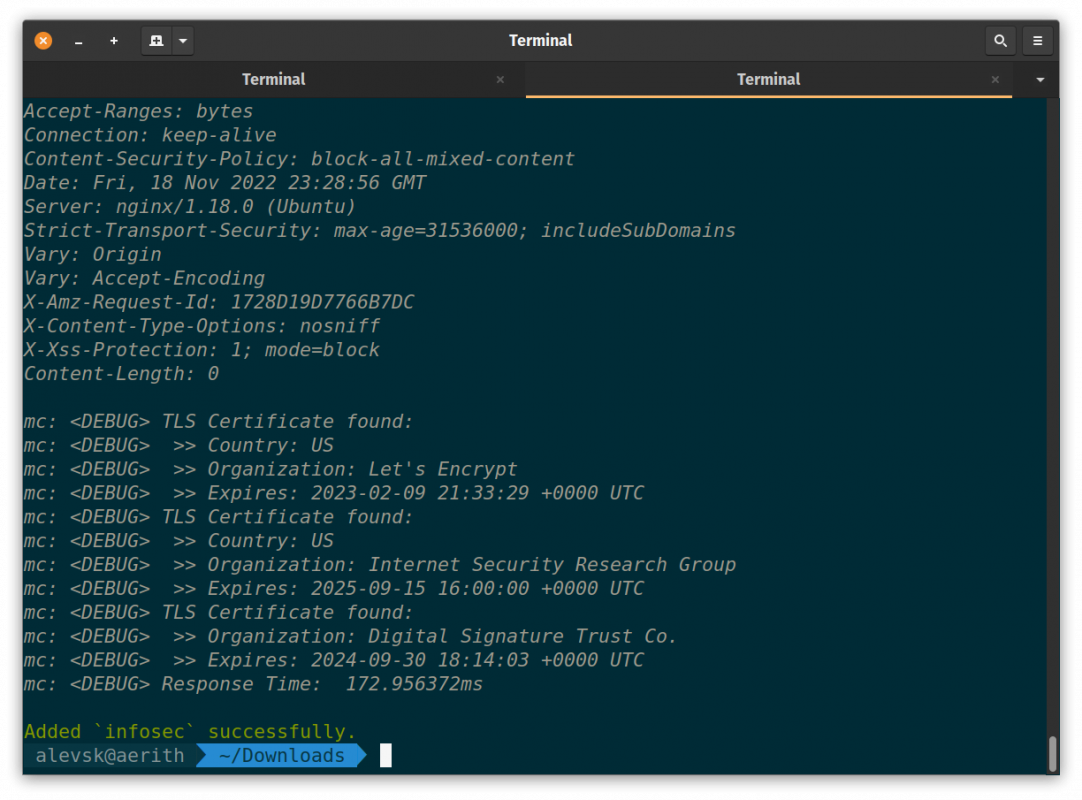
That was expected since I knew s3 clients don’t need any authentication to download content from the buckets. WIth this I was able to list all the content at https://media.infosec.exchange/infosecmedia.
mc ls infosec/infosecmedia
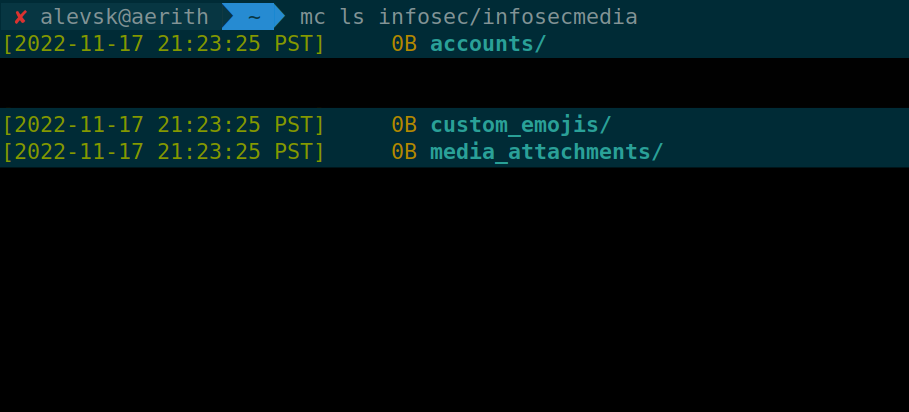
I noticed there were additional folders in there and I could access them with anonymous credentials as well, this will be equivalent to a Directory Traversal vulnerability.
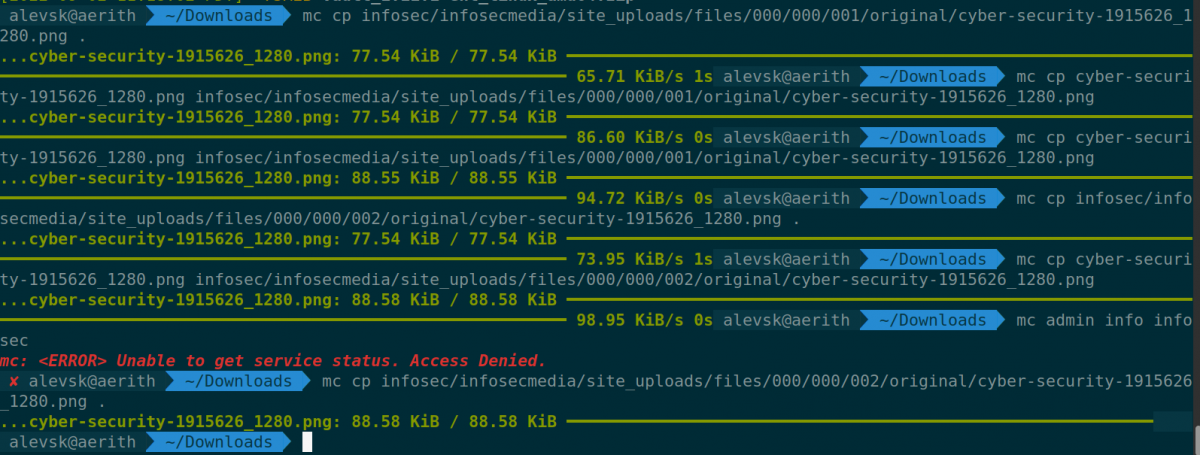
So far I tried read and list operations only, in S3 IAM policies language that would be the Get and List Object operation, but what about Create/Upload and Delete?.
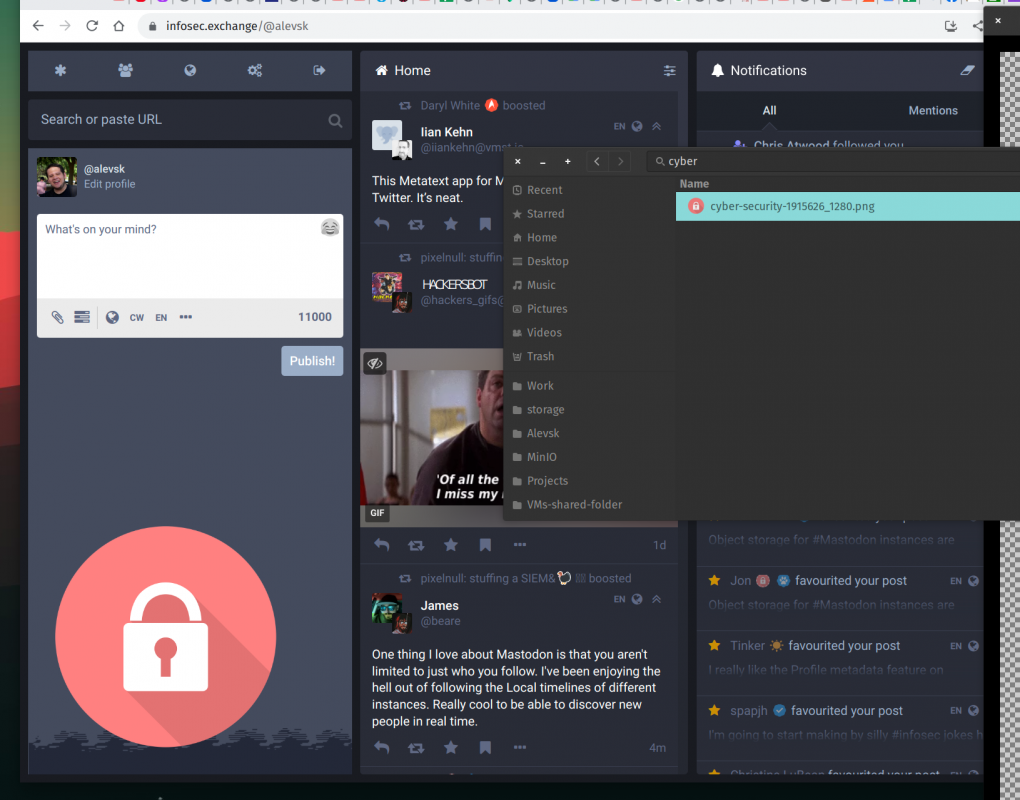
I identified where the logo of the server was stored inside the https://media.infosec.exchange/infosecmedia server, I downloaded it with mc, modified it a little bit and uploaded the modified version and it works!
Original:
Modified:
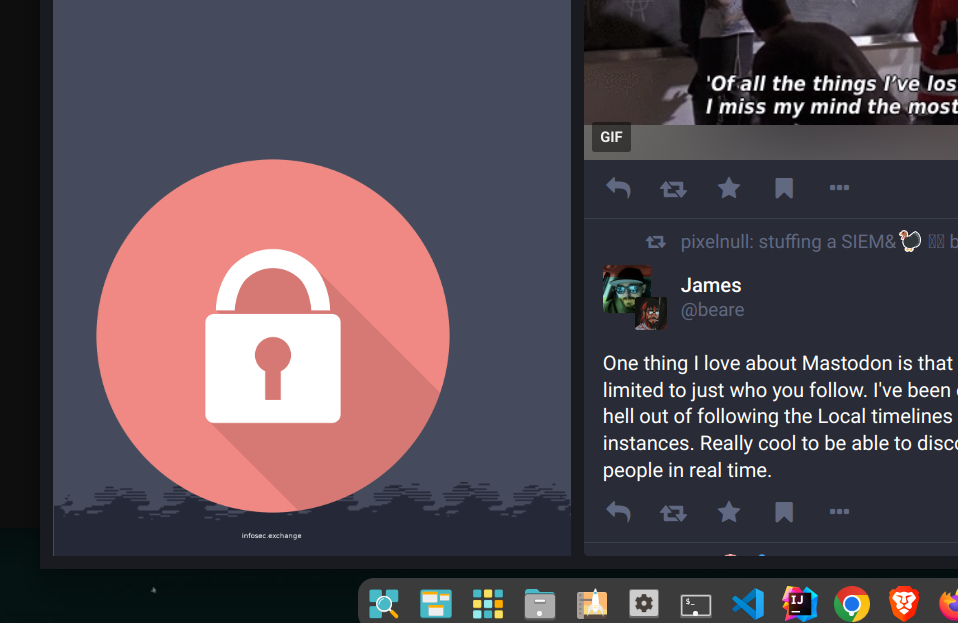
I added a tiny label at the bottom of the logo that says infosec.exchange so the change will go unnoticed and because my intention was never to disrupt the server.
At this point I realized the anonymous credentials has s3:* privileges, and I can do everything I want content wise, including:
- Download all the files in the server, including files shared via Direct Messages.
- Delete all the files in the server
- Replace everyone’s profile picture with an Elon Musk meme, jk but it was possible to replace all the existing files
This system misconfiguration at the object storage level defeats whatever security mechanism Mastodon has on top.
Timeline of events and disclosure
- 11/17/2022 – I created my infosec.exchange account and start playing around
- 11/17/2022 – Found anonymous access was enabled and all the files were exposed
- 11/17/2022 – Reached to [email protected] and reported the issue
- 11/18/2022 – Jerry confirmed is aware of the issue and working on a fix
- 11/18/2022 – Issue got fixed, thank you so much Jerry.
After reporting this issue I wondered if there may be other Mastodon instances with the same issue (system misconfiguration) so I went to fediverse.space and started checking some of the most popular, I found similar problems with a couple of them and I already reported the vulnerabilities.
Happy hacking